Related searches:
PHP errors and exception handling
Author: bamboo06 on 9-06-2020, 20:26, views: 1974
0
Unlike other programming languages that throw exceptions when encountering errors, PHP also has an exception mechanism when handling objects, but PHP will perform as happily as possible and ignore what happened, unless it encounters an extremely serious error. There is an exception. This article outlines PHP-related error exception handling mechanisms.
PHP has several error severity levels. The three most common types of information are errors, notices, and warnings. They have different severity: E_ERROR, E_NOTICE and E_WARNING. The error is a serious problem during operation, usually caused by code error, it must be corrected, otherwise PHP will stop execution. Notifications are information of a recommended nature, because the program code may cause problems during execution, but the program will not stop. The warning is a non-fatal error, and program execution will not be aborted.
PHP has several error severity levels. The three most common types of information are errors, notices, and warnings. They have different severity: E_ERROR, E_NOTICE and E_WARNING. The error is a serious problem during operation, usually caused by code error, it must be corrected, otherwise PHP will stop execution. Notifications are information of a recommended nature, because the program code may cause problems during execution, but the program will not stop. The warning is a non-fatal error, and program execution will not be aborted.
Category: PHP Scripts
PHP security of the password hashing
Author: bamboo06 on 14-08-2019, 18:29, views: 1207
0
Never know the user's password, we must encrypt the user's password, and can not save the user's original password directly in the database. Do not limit the user password format. If the format is specified, it may be exploited and cracked by the attacker. Of course, we need to limit the minimum length of the password. It is recommended to use at least 8 bits. The longer the better.

For password security, developers need to:
1, absolutely can not know the user's password, we must encrypt the user's password, can not save the user's original password directly in the database.
2, do not limit the user password format, if the format is specified, it is likely to be exploited and cracked by the attacker, of course, we need to limit the minimum length of the password, it is recommended to at least 8 bits, the longer the better.
3, can not send the user password through the mailbox, when we develop the application to retrieve the password, the user password is not notified to the user by email, but the link to reset the password is sent to the user in the form of mail, let the user Go to reset the password.

For password security, developers need to:
1, absolutely can not know the user's password, we must encrypt the user's password, can not save the user's original password directly in the database.
2, do not limit the user password format, if the format is specified, it is likely to be exploited and cracked by the attacker, of course, we need to limit the minimum length of the password, it is recommended to at least 8 bits, the longer the better.
3, can not send the user password through the mailbox, when we develop the application to retrieve the password, the user password is not notified to the user by email, but the link to reset the password is sent to the user in the form of mail, let the user Go to reset the password.
Category: PHP Scripts
PHP security data filtering and verification
Author: bamboo06 on 28-07-2019, 18:26, views: 1377
0
Never trust external input, don't trust any data from a data source that is not under your direct control. In actual development, there is always someone intentionally or unintentionally injecting dangerous data into PHP code, so PHP security programming becomes important. Generally, we deal with external input security ideas: filtering input and verifying data.
Filtering input means escaping or deleting characters that are not safe from external data.
Filtering input means escaping or deleting characters that are not safe from external data.
Category: PHP Scripts
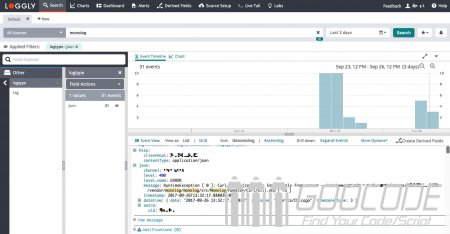
Monolog-PHP log class library introduction
Author: bamboo06 on 2-12-2018, 17:47, views: 1924
0
Monolog is a full and easy to expand log log library under php. There are many well-known php frameworks including Symfony, Laravel, CakePHP and so on that have Monolog built in. Monolog can send your logs to files, sockets, inboxes, databases and various web services.
Monolog follows the PSR3 interface specification and can be easily replaced with other log classes that follow the same specification. Monolog has good extensibility. Through the interfaces Handler, Formatter and Processor, you can expand and customize the Monolog library.
Monolog follows the PSR3 interface specification and can be easily replaced with other log classes that follow the same specification. Monolog has good extensibility. Through the interfaces Handler, Formatter and Processor, you can expand and customize the Monolog library.
Category: PHP Scripts / Plugins
Talk about meta tags
Author: bamboo06 on 9-04-2017, 00:20, views: 14848
0
The Meta tag is an auxiliary tag for the HTML language head area, which is located between the head tag and the title tag in the head of the HTML document, which provides information that is not visible to the user. It can be used for browsers (how to display content or reload pages), search engines (keywords), or other web services.
I am now front-end page development often used meta tag content compiled into the mobile side of the web development meta information for the needs of access.
I am now front-end page development often used meta tag content compiled into the mobile side of the web development meta information for the needs of access.
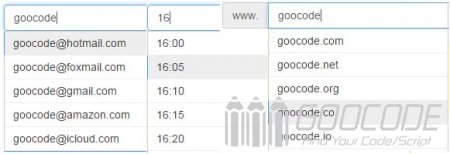
jQuery autocomplete plugin: completer
Author: bamboo06 on 17-08-2016, 00:31, views: 3458
8
When we input forms, such as entering the mail name and the next words are autocompleted, the content will automatically shown and several commonly used mailboxes are listed, and the user simply selects what he will enter. Inputs in this case are time, and domain names. All this can be done automatically by the plug-completer to help you achieve.
Category: Javascript / Plugins
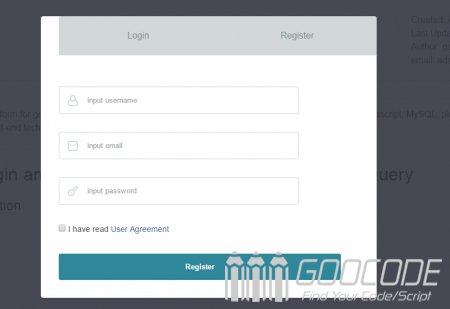
Switching Login and registration form in pop-up window by jQuery
Author: bamboo06 on 10-08-2015, 00:38, views: 12506
11
When you click on a page log-in or register button it will pop up a modal window which is a pop-up layer, we can easily switch on the popup login and registration form, a great convenience to users, without shutting down the floor to go click on to other operations, on many sites it has been widely used.
We will use examples to achieve this effect by using jQuery, CSS3 and HTML5 technologies.
We will use examples to achieve this effect by using jQuery, CSS3 and HTML5 technologies.
Category: Javascript / CSS / HTML5
PBN(Private Blog Network) Strategy
Author: bamboo06 on 18-12-2014, 02:50, views: 2618
7
This article discusses how to go through the PBN only do SEO, regards for PBN's attitude problems, such as "PBN is dead", "PBN is still valid," and so on, eyes of the beholder, the wise see wisdom.
Well, let's start the topic - Private Blog Network Strategy.
Well, let's start the topic - Private Blog Network Strategy.
Category: Internet
Cloud Computing and SME management
Author: bamboo06 on 13-12-2014, 02:12, views: 2220
4
Everyone knows that the winds of cloud computing has arrived. In 2014 about the past, a number of cloud computing products or services look like hail, crackling fall down. Foreign Amazon, Google, IBM, Microsoft, and other domestic giants BAT stop staking, cloud computing market to determine the basic pattern, whether it is a public cloud, private cloud or hybrid cloud the basic structures have been basically completed.
Cloud computing market, a distance, a thriving event.
However, in the rapidly growing popularity of cloud computing moment, giants and big business peacefulness, Tuibeihuanzhan, while the number of SMEs had to face the difficult problem of cloud computing by agents.
Cloud computing market, a distance, a thriving event.
However, in the rapidly growing popularity of cloud computing moment, giants and big business peacefulness, Tuibeihuanzhan, while the number of SMEs had to face the difficult problem of cloud computing by agents.
Category: Internet
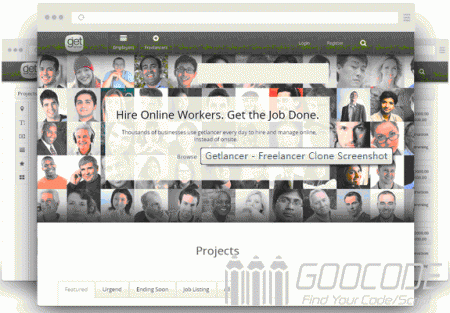
8 nice looking freelancer clone php scripts
Author: bamboo06 on 31-10-2014, 23:40, views: 5465
19
Getlancer - Freelancer Clone
Agriya’s Getlancer is the remarkable freelancer clone script which is competently offering all the beneficial and key features of many leading freelancing websites like freelancer.com, Elance, oDesk and guru. It assists the entrepreneurs to bring their excellent website like freelancer within a few days. This script also appends many fresh and significant features like simple bidding system, dispute management system, internal messaging system, project milestones, escrow system, admin dashboard and many other interesting features for the smooth functioning of your website working as freelancer management.
Agriya’s Getlancer is the remarkable freelancer clone script which is competently offering all the beneficial and key features of many leading freelancing websites like freelancer.com, Elance, oDesk and guru. It assists the entrepreneurs to bring their excellent website like freelancer within a few days. This script also appends many fresh and significant features like simple bidding system, dispute management system, internal messaging system, project milestones, escrow system, admin dashboard and many other interesting features for the smooth functioning of your website working as freelancer management.
Category: PHP Scripts